Bitcoin, launched in 2008 by an unidentified person or group named Satoshi Nakamoto, has become the most popular cryptocurrency globally. Its core is an advanced algorithm that guarantees safe, decentralized transactions independent of any one entity, such as a government or bank. The blockchain is a digital database that keeps track of all Bitcoin transactions—this algorithm controls it. This article will delve into the Bitcoin Algorithm’s complexities, covering its cryptographic underpinnings, transaction processing, mining, and the wider cryptocurrency ecosystem.
Blockchain technology and a consensus method known as Proof of Work (PoW) form the basis of the Bitcoin algorithm. A “blockchain” is just a series of “connected “blocks that record verified financial transactions.” Bitcoin’s use of encryption guarantees the immutability, transparency, and security of the blockchain. The goal of Bitcoin’s algorithm is to keep the network decentralized. Miners, on the other hand, compete by solving cryptographic riddles to add blocks to the chain. Bitcoin can safely operate thanks to its decentralized method, eliminating the need for intermediaries such as banks.
Cryptographic Foundations
Digital signatures and hashing are two of the most fundamental cryptographic methods the Bitcoin algorithm uses extensively.
Hashing (SHA-256)
The process of hashing involves passing an input, like Bitcoin transaction data, through a mathematical function to generate an output of a fixed size; in this instance, that value is 256 bits. For this purpose, Bitcoin employs the Secure Hash Algorithm, SHA-256. A hash is a one-of-a-kind, 64-character hexadecimal string; the SHA-256 algorithm can take any input and generate one. Because each hash is distinct, slightly altering the input will result in a very different hash. Hashes are employed in the Bitcoin blockchain to guarantee that data remains intact. To connect all blocks, each includes a hash of the one before. This renders it extremely difficult, if not impossible, to change a single transaction without recalculating all hashes that follow it.
Digital Signatures (ECDSA)
The Elliptic Curve Digital Signature Algorithm (ECDSA) is another mechanism Bitcoin uses to guarantee that transactions are legitimate. To send Bitcoin, a user must first sign the transaction using their private key. By utilizing the matching public key, third parties can validate the signature and confirm that the sender has authorized the transaction.
This cryptographic method verifies that a Bitcoin wallet can only be accessed by its legitimate owner for further safety and to forestall fraud.
Transactions and Bitcoin Algorithm
Bitcoin’s multi-stage transaction processing guarantees immutability, decentralization, and security. A streamlined explanation of the transaction procedure is as follows:
- Initiating a Transaction: When a user decides to send Bitcoin, they create a transaction message that includes information such as the recipient’s address, the amount of Bitcoin, and a digital signature from their private key. This transaction is broadcast to the Bitcoin network.
- Transaction Propagation: The transaction is propagated across the Bitcoin network, where it is picked up by nodes (computers running the Bitcoin software). These nodes verify the transaction’s authenticity by checking the sender’s digital signature and ensuring they send sufficient funds to their wallet.
- Proof of Work: When combined with the block data, the Bitcoin algorithm’s Proof of Work mechanism requires a nonce—a random number that produces a hash that meets specific difficulty requirements. This hash must start with a specified number of leading zeros. Finding this hash requires massive computational power, as miners must go through trillions of possible nonces before finding the correct one.
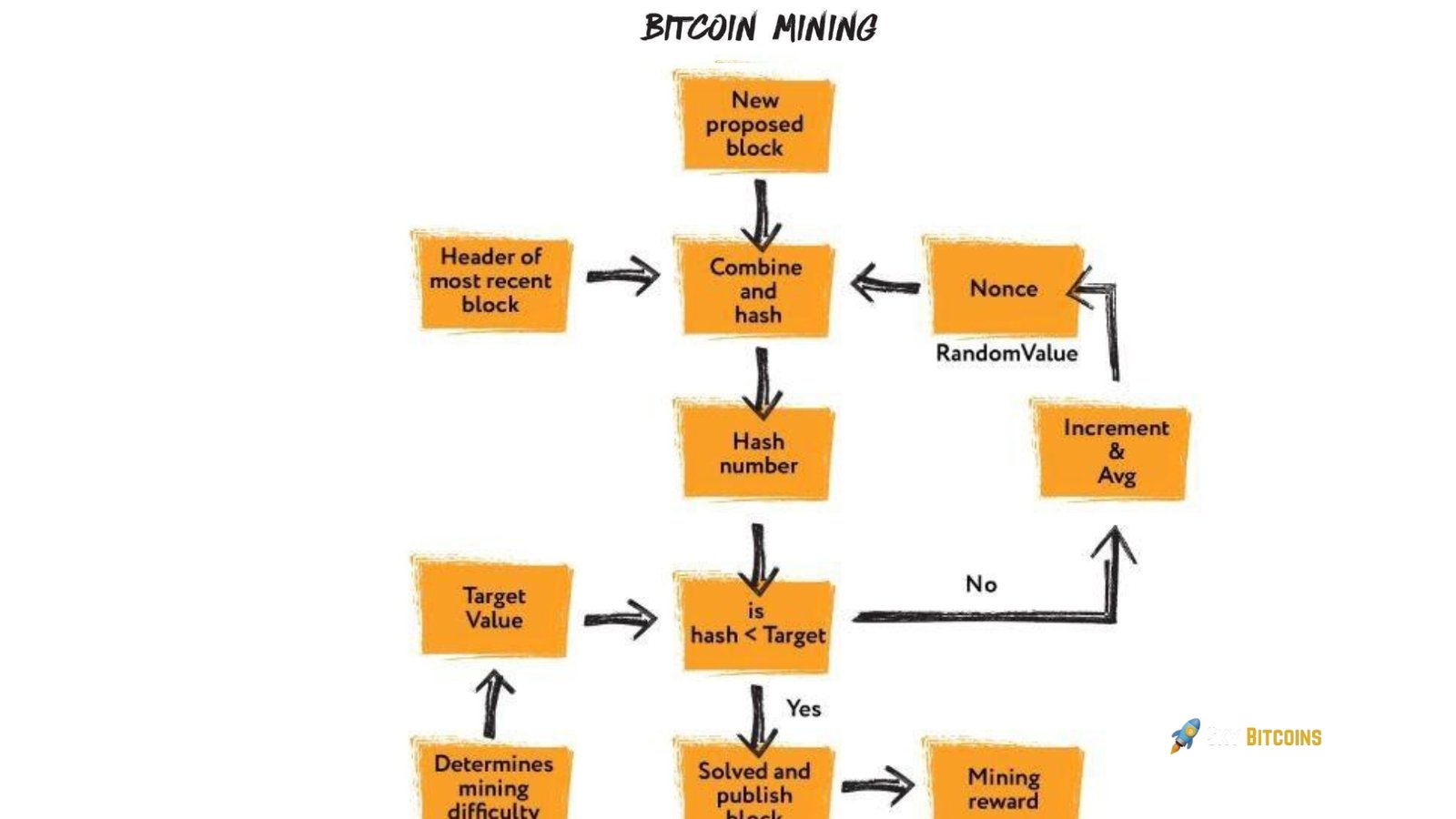
- AddiBlocke Block to the Blockchain: The TBlockw block is added once a miner finds the correct solution. The Blockh block contains a reference (hash) to the prBlocks block, creating a chain of cryptographically linked blocks. This structure ensures that any attempt to alter a block would require recalculating all subsequent blocks, making tampering virtually impossible.
- Transaction Confirmation: The transaction is now considered confirmed, with each additional block added to the chain providing further confirmation. A transaction is usually considered fully secure after six confirmations (six new blocks added to the chain), as it becomes increasingly difficult for an attacker to reorganize the blockchain.
The Role of Mining in Bitcoin’s Algorithm
Mining is a critical part of Bitcoin’s algorithm, serving two main purposes: maintaining the network and introducing new bitcoins into circulation.
Securing the Network
Mining verifies each transaction before adding it to the blockchain. To prevent unscrupulous actors from readily manipulating the blockchain, the Proof of Work mechanism makes the computational expense of adding new blocks high. Because of this distributed system, no one entity can ever take over the network.
Bitcoin Rewards
The Bitcoin algorithm rewards miners with newly created bitcoins (the block reward) and transaction fees to encourage them to keep mining. The Bitcoin Halving occurs every four years and halves the block reward, which started at 50 bitcoins in 2009. The block reward has been set at 6.25 bitcoins as of 2024 and will gradually fall in subsequent years. Bitcoin is deflationary by design because of its unique regulated diminishing supply. The last Bitcoin is anticipated to be mined around 2140, and the maximum supply is 21 million.
Difficulty Adjustment in Bitcoin’s Algorithm
Bitcoin’s algorithm uses Bitcoin’s adjust mechanism to produce blocks every 10 minutes regardless of the network’s computational capability. Based on the network’s hash rate, the algorithm adjusts mining difficulty every 2016 block, or two weeks.
As more miners join the network and the hash rate rises, mining new blocks becomes tougher. Cryptographic riddles are easier to solve when the hash rate drops. The dynamic adjustment stabilizes block generation time, preventing mining activity from affecting Bitcoin’s supply rate. The algorithm makes it difficult to encourage miners to secure the network while avoiding Bitcoin inflation. It keeps the blockchain secure and decentralized, independent of miner participation.
Bitcoin Algorithm and Security
Bitcoin’s decentralization and Proof of Work, as well as Bitcoin’s consensus method, make it secure. Miners use much computer power to solve cryptographic riddles and add new validated transactions to the blockchain. This makes changing the blockchain difficult because an attacker must control over 50% of the network’s computational power, a 51% attack. Network’s assault becomes impractical as Bitcoin’s network grows due to the mining power.
Bitcoin also uses SHA-256 hashing and ECDSA digital signatures to avoid double-spending and verify transactions. Senders sign and link transactions to earlier blocks, creating an immutable chain. These strong security mechanisms protect the Bitcoin network from fraud, manipulation, and illegal access, ensuring trust in the decentralized system.
Limitations and Future Developments
Bitcoin’s algorithm has constraints despite Bitcoin’s decentralization and security. The network’s processing speed of 7 transactions is shockingly slow compared to Visa, making scalability the key challenge. With Bitcoin’s growing popularity, transaction confirmation times have increased during high demand. Developers are considering layer-2 protocols like the Lightning Network to solve these issues. This protocol would execute transactions off-chain and only settle on the Bitcoin blockchain when necessary, making them cheaper and faster. The latest Bitcoin code modification, Taproot, increases privacy and efficiency, allowing more complex transactions at lower rates.
Conclusion
Bitcoin is secure, decentralized, and transparent due to its algorithm. Bitcoin’s Proof of Work (PoW) consensus mechanism, Bitcoin’s SHA-256 cryptographic hashing protects the blockchain from fraud and manipulation. Adjusting the difficulty level guarantees a consistent mining experience and the fact that the network is decentralized means that no one can manipulate it. Despite scalability issues and excessive energy consumption, the Bitcoin algorithm has survived. The Lightning Network and Taproot protocol improvements try to overcome these constraints. The Bitcoin algorithm’s security, transparency, and design have made it the backbone of the cryptocurrency economy, enabling decentralized finance to flourish and evolve.



